Enforce Kubernetes Policies Easily with Kyverno
Kubernetes natively validates resource manifests like deployments to ensure they are syntactically correct. For example, if you try to create a deployment with a syntax error in your deployment.yaml, Kubernetes will reject it. However, once syntax is correct, Kubernetes doesn’t prevent you from deploying applications into the wrong namespace or without proper labels — things that can break your app connectivity or organizational standards.
This is where Kyverno comes in. Kyverno is a powerful Kubernetes policy engine that helps enforce policies and best practices across your cluster — validating, mutating, and generating resources automatically.
Why Kyverno?
Imagine these scenarios:
- What if an application gets deployed into the wrong namespace?
- What if a deployment is missing essential labels to connect to a service?
- What if your organization requires strict policies but you can’t manually monitor all deployments and pods?
Kyverno lets you codify these rules as Kubernetes policies that are automatically enforced, so your cluster stays consistent and compliant.
Getting Started with Kyverno
You can follow along with the Kyverno GitHub repo here or use the code snippets below.
Before we proceed, make sure you have:
- Kubernetes installed (for example, via MicroK8s)
- Helm installed for package management
Here are reference blogs if you need a refresher:
Kubernetes Reference Blog
Helm Reference Blog
If you are using MicroK8s, it’s handy to alias kubectl for easier commands:
alias kubectl="microk8s kubectl"Installing Kyverno
helm repo add kyverno https://kyverno.github.io/kyverno/
helm repo update
helm install kyverno kyverno/kyverno -n kyverno --create-namespace
Sample Deployment File
Save the following deployment manifest as deployment.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: react-deployment
namespace: react-microk8s
labels:
app: react-demo
spec:
replicas: 2
selector:
matchLabels:
app: react-demo
template:
metadata:
labels:
app: react-demo
spec:
containers:
- name: react-demo
image: sagarkakkalasworld/react-microk8s
ports:
- containerPort: 80
Create Namespace
Since this deployment targets the react-microk8s namespace, create it first:
kubectl create ns react-microk8sKyverno Validation Policy: Require Namespace on Deployments
Let’s create a Kyverno ClusterPolicy that enforces deployments must specify a namespace other than the default.
Save this as require-namespace-policy.yaml :
apiVersion: kyverno.io/v1
kind: ClusterPolicy
metadata:
name: require-namespace-on-deployments
spec:
validationFailureAction: Enforce
rules:
- name: must-specify-namespace
match:
any:
- resources:
kinds:
- Deployment
validate:
message: "All Deployments must specify a namespace (not use the default)."
deny:
conditions:
- key: "{{ request.namespace }}"
operator: Equals
value: "default"
Apply the policy:
kubectl apply -f require-namespace-policy.yamlTest the Validation Policy
Edit your deployment.yaml to comment out or remove the namespace field:
metadata:
name: react-deployment
#namespace: react-microk8s
labels:
app: react-demo
Try to apply it:
kubectl apply -f deployment.yamlYou should see an error:
error: admission webhook "validate.kyverno.svc" denied the request: All Deployments must specify a namespace (not use the default).
Now, uncomment the namespace and apply again:
kubectl apply -f deployment.yaml
This time the deployment will succeed.
Kyverno Mutation Policy
Kyverno also supports mutation policies that modify resources before they get created.
For example, say your organization requires every deployment to have at least 3 replicas. Even if someone specifies 2 replicas, Kyverno can automatically mutate it to 3.
Save this as mutate-deployment-replicas.yaml:
apiVersion: kyverno.io/v1
kind: ClusterPolicy
metadata:
name: set-deployment-replicas
spec:
rules:
- name: set-replicas-to-3
match:
resources:
kinds:
- Deployment
mutate:
patchStrategicMerge:
spec:
replicas: 3
Apply the mutation policy:
kubectl apply -f mutate-deployment-replicas.yamlNow apply your original deployment.yaml with 2 replicas:
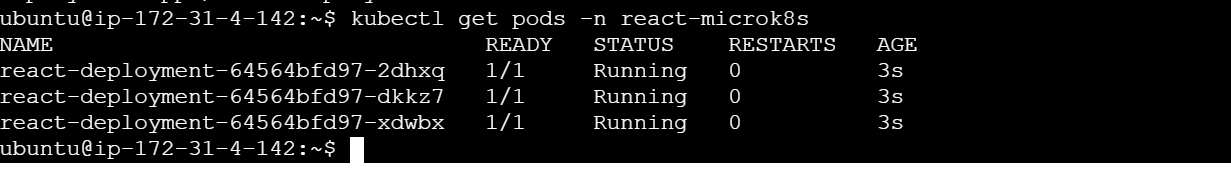
kubectl apply -f deployment.yaml
Kyverno will mutate the deployment and set the replicas to 3 automatically. Verify by checking pods:
kubectl get pods -n react-microk8sYou will see 3 pods running, as per policy.
Clean Up
To delete a cluster policy:
kubectl get clusterpolicykubectl delete clusterpolicy $POLICY-NAMEExplore More
Try other Kyverno policies from the Kyverno repo and tailor your cluster governance to your organization’s needs.
Kyverno makes policy enforcement in Kubernetes simple, automated, and powerful — helping you maintain consistency and compliance effortlessly.











Very interesting and detailed post! I learned a lot from this. Your blog always provides helpful information. Keep up the excellent work and consistent updates!
ReplyDeleteBirthday Party Venues in Gurgaon
Farmhouse in Gurgaon for Party
Private party places in Gurgaon